
Online censorship detector aims to make the internet a freer place
Censored Planet could provide new insight into the flow of online information

Censored Planet could provide new insight into the flow of online information
In an advance that could one day provide a comprehensive, publicly available window into worldwide internet censorship, a team of researchers at the University of Michigan has turned public internet servers across the globe into automated sentries that can monitor and report when access to websites is being blocked.
Censored Planet, a first-of-its-kind system, has begun collecting data on three different types of internet censorship tactics commonly used by governments and others. Roya Ensafi, a research assistant professor of computer science and engineering and project leader, says it’s a major step forward for online transparency and accountability.
“Currently, censorship researchers must rely on anecdotal information collected from a handful of human volunteers working inside countries where censorship is happening,” she said. “One or two people manually visiting websites can only collect a tiny snapshot of information, and they’re often in danger of reprisals from the government if they’re found out. Censored Planet, on the other hand, could have hundreds of electronic vantage points in a given country. It’s more ethical, safer, and because it reports consistently, it could provide the first comprehensive picture of how censorship evolves over time.”
The project is the culmination of an effort that began in 2009, when Ensafi moved from her native Iran to the United states for graduate school. She developed the basic principles that underpin the project during her time as a graduate student at the University of New Mexico, as a research intern at the University of California, Berkeley and as a postdoctoral researcher at Princeton University.
“As an undergrad in Iran, there were a lot of online resources that I didn’t have access to—the Olympics website, web tools I needed in my studies and many other examples,” she said. “I never knew who was blocking me or why, and that was frustrating. I was also frustrated by the work that was being done to study censorship. Researchers were drawing very broad conclusions from very narrow data, almost always focused on Iran and China. Censorship is a global phenomenon and we need to be able to see what’s happening globally to put it in perspective.”
Censorship is a global phenomenon and we need to be able to see what’s happening globally to put it in perspective.
Roya Ensafi
At U-M, Ensafi and her team developed a suite of three tools, each of which plays a different role in monitoring worldwide internet censorship.
w chance of them being traced back to any one person. In addition, they must follow current internet protocol, and be reliable and stable enough to be used for regularly monitoring censorship. They’re often located at universities or run by the internet service providers that make up the backbone of the internet.
Once the system has established a network of reflectors—which can be done in a matter of hours—it instructs them to attempt to reach a list of selected web addresses. By analyzing the information that comes back, the tools can determine whether and how those addresses are being blocked.
In The News
NATIONAL PUBLIC RADIO
FEBRUARY 7, 2019
Ensafi says that because the tools use the same internet protocols as any other machine and take up very little bandwidth, they don’t interfere with or slow down normal activity on the vantage points. The requests make up only a tiny fraction of the millions that a given server receives every day.
“In the universe of internet traffic, these requests are like a single atom,” Ensafi said. “Nation-states have so much traffic to deal with that it’s extremely difficult to detect what we do.”
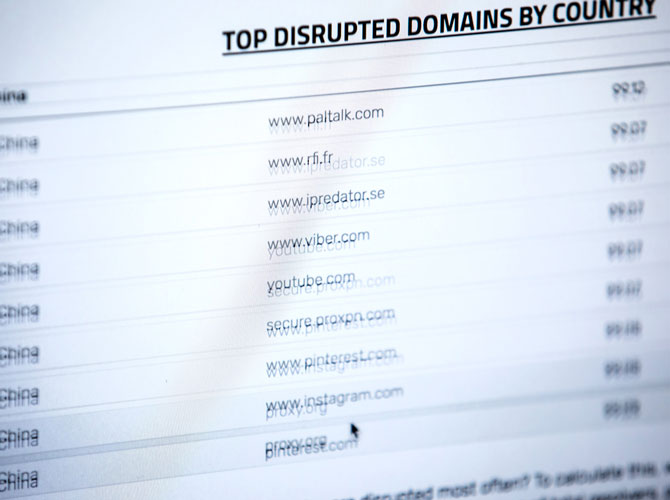
Currently, the team is conducting preliminary scans to verify the tools’ effectiveness and evaluate how to use the data that they produce. The data they’ve collected is publicly available at censoredplanet.org, including a list of the most-blocked websites in monitored countries. Ensafi cautions, though, that it’s too early to draw conclusions about censorship from it.
“Just because a site shows up as being blocked in a certain country doesn’t necessarily mean it’s being censored,” she explains. “For example, imagine that a website shows up on our list as ten percent blocked in a given country. That could mean that we have ten vantage points inside that country and it’s being blocked on one of them. There are any number of possible reasons for that. Maybe one vantage point is at a university that has its own web filtering system, or maybe the site and our reflector use incompatible protocols. But if a site shows up as blocked on nine out of ten servers in a given country, that’s a pretty good sign that there’s an effort being made to suppress it.”
They’re working with computer science and political science researchers to further refine the tools. Today, they’re scanning a pre-selected list of around 4,000 commonly censored websites, but they hope to eventually scan millions of sites, and to be able to accept requests from researchers to monitor specific sites.
A paper on Quack, the newest Censored Planet tool, was presented at the 27th Usenix Security Symposium in Baltimore, Maryland on August 15, 2018. Titled “Quack: Scalable Remote Measurement of Application-Layer Censorship,” it was supported by the National Science Foundation (grants CNS-1409505, CNS-1518888 and CNS-1755841) and by a Google Faculty Research Award.